When Code Breaks Economies
The cybersecurity threat isn't just limited to your emails and DMs!
At ReadOn, we don’t just report the markets. We help you understand what truly drives them, so your next decision isn’t just informed, it’s intelligent.
On August 2025, Britain’s largest carmaker, Jaguar Land Rover, went dark. Not a metaphorical darkness. Actual production halt. Five weeks of zero output across global operations. The culprit? A cyberattack that cascaded through 5,000 suppliers, costing the company £196 million directly and bleeding £1.9 billion from the UK economy.
That’s from a single breach.
Now imagine this. What if a similar attack hit the Reliance supply chain? Or Maruti Suzuki’s vendor network spanning hundreds of SMEs across Gujarat and Haryana? The World Economic Forum’s Global Cybersecurity Outlook 2026, released this January, suggests we shouldn’t treat this as a hypothetical. The threat landscape has fundamentally shifted.
The AI Arms Race Nobody Saw Coming
94% of global executives surveyed believe AI will be the most significant driver of change in cybersecurity this year. Not cloud. Not quantum computing. AI.
But here’s the twist. AI isn’t just the solution. It’s also increasingly becoming the problem.
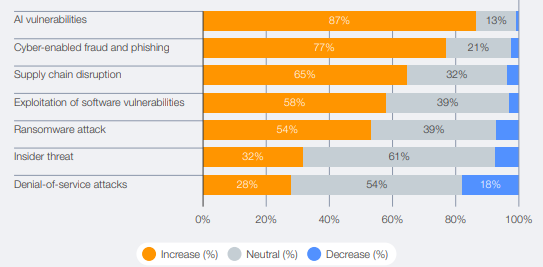
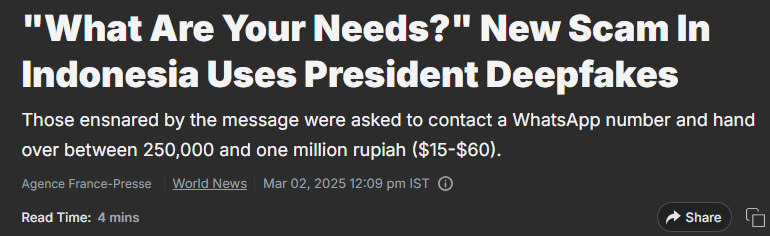
Some 87% of respondents identified AI-related vulnerabilities as the fastest-growing cyber risk over 2025. That’s a remarkable shift. Criminal networks are now using generative AI to craft phishing emails so sophisticated that they mimic the writing style of your actual colleagues. They’re deploying deepfake audio to impersonate CEOs approving fraudulent wire transfers. In Indonesia, scammers created deepfake videos of President Prabowo Subianto promising financial aid, duping citizens across 20 provinces.
The barrier to entry for cybercrime has collapsed. A non-tech expert in a tier-3 city can now access AI tools that rival what nation-states possessed five years ago.
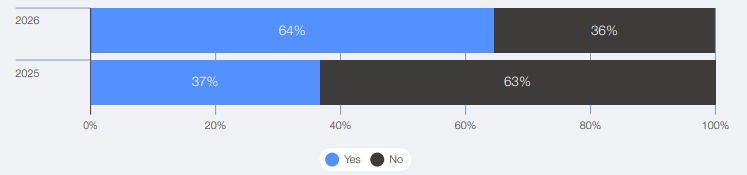
The good news? Defenders are catching up. The share of organisations assessing AI security before deployment nearly doubled from 37% in 2025 to 64% in 2026. But there’s a catch. More than half (54%) cited insufficient knowledge and skills as their primary obstacle to deploying AI-driven cybersecurity solutions. The technology exists. The people who understand it don’t.
The Fraud Epidemic in Your Inbox
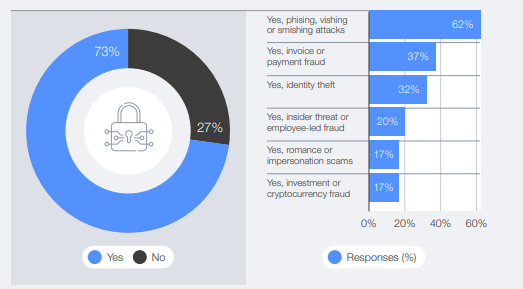
Let’s talk about something closer to home. In the survey, 73% of respondents said they or someone in their network had been personally affected by cyber-enabled fraud in the past year. Phishing attacks topped the list at 62%, followed by payment fraud at 37% and identity theft at 32%.
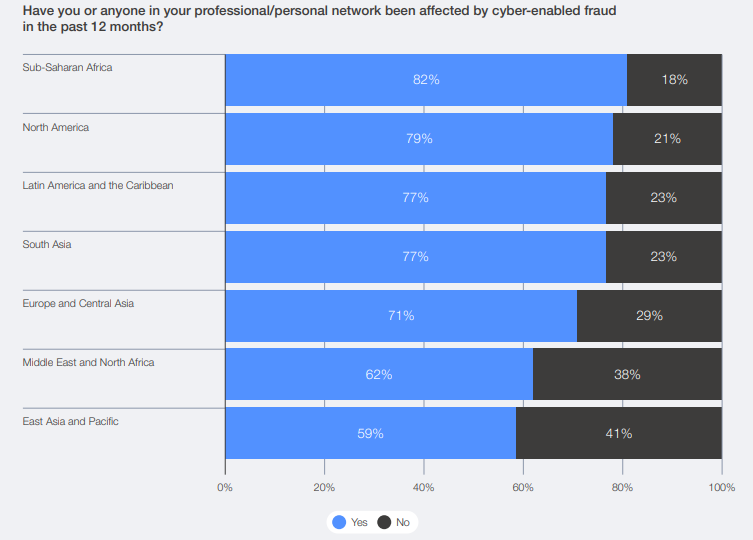
And this isn’t just hitting large corporations. Sub-Saharan Africa reported the highest exposure at 82%, followed by North America at 79%. Cybercriminals are increasingly targeting regions with growing digital adoption but immature security infrastructure.
Sound familiar? India’s digital payments ecosystem processed over ₹200 lakh crore in UPI transactions. We’ve built remarkable digital infrastructure at scale, but our cyber defences haven’t kept pace.
The report notes that CEOs have shifted their primary concern from ransomware to cyber-enabled fraud. That’s not because ransomware disappeared. It’s because fraud now hits closer to the bottom line and affects a wider base from boardrooms to household savings.
When Geopolitics Becomes Your IT Problem
There’s another uncomfortable truth in this report. Cybersecurity is no longer just a technical function, it’s geopolitical.
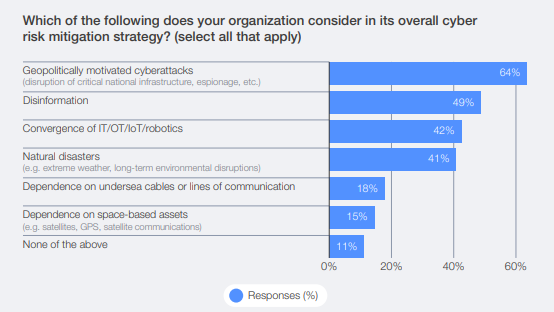
Some 64% of organisations now account for geopolitically motivated cyberattacks in their risk mitigation strategies. Think disruption of critical infrastructure, espionage, state-sponsored hacking. And 91% of the largest organisations (those with over 100,000 employees) have changed their cybersecurity strategies specifically because of geopolitical volatility.
What does this mean for India? Consider the submarine cable routes that carry 99% of our international internet traffic. Or our dependence on foreign cloud providers for critical government and enterprise data.
The report reveals that only 18% of organisations consider undersea cable dependencies in their cyber risk planning. Only 15% account for space-based assets like GPS and satellite communications. These aren’t exotic concerns. A coordinated attack on submarine cables could isolate India’s digital economy within hours.
In April 2025, Russian hackers breached a Norwegian hydroelectric dam, remotely opening a floodgate and releasing 500 litres of water per second for four hours. It wasn’t about the water. It was a message that critical infrastructure is vulnerable.

The Skill Gap
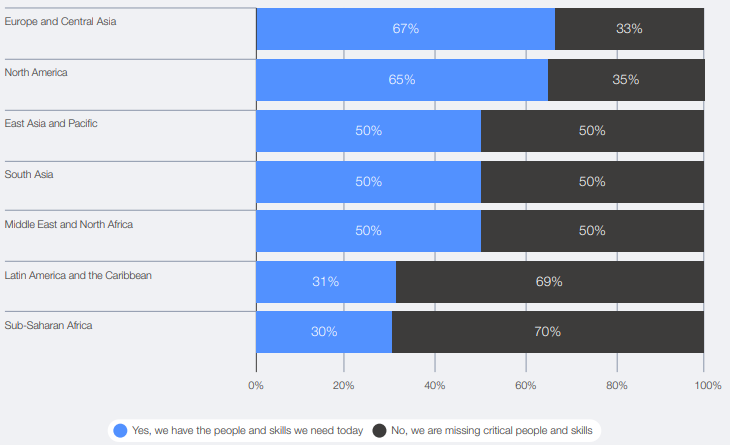
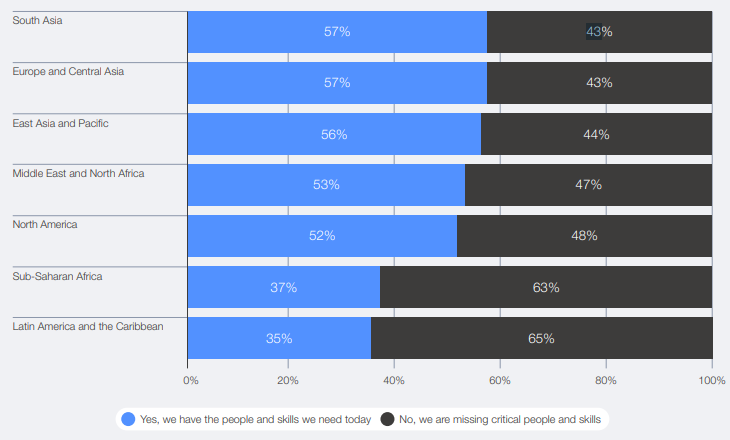
The report shows that 70% of CEOs in sub-Saharan Africa and 69% in Latin America lack the cybersecurity skills to meet their current objectives. By comparison, only 33% in Europe and 35% in North America report similar gaps.
India isn’t broken out separately, but the South Asia data tells the story. 43% of organisations report missing critical people and skills. And when you segment by resilience levels, the picture gets clearer. Among organisations with insufficient cyber resilience, 85% cited skills shortages as a key barrier.
The top three cybersecurity roles experiencing shortages globally are threat intelligence analysts, DevSecOps engineers, and identity and access management specialists. They require specialised training, continuous upskilling, and critically, experience with real-world incident response.
There’s a compounding effect too. Organisations that lack skills also lack the resources to attract talent. They can’t compete with the Googles and Microsofts of the world for top security engineers. So the gap widens. And in an interconnected digital supply chain, your weakest vendor becomes everyone’s vulnerability.
The Supply Chain Problem
The Jaguar Land Rover incident exposed how modern businesses are essentially constellations of interconnected systems. A single compromised supplier can cascade into catastrophic failure.
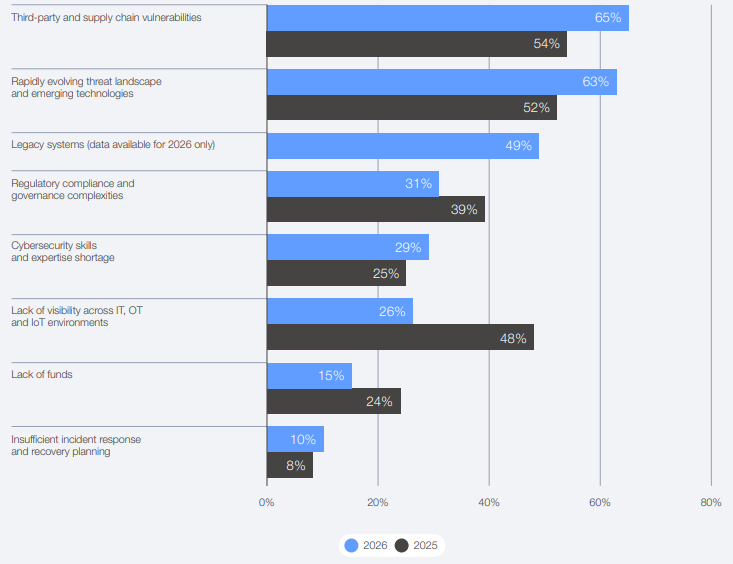
The report is blunt. 65% of large companies now cite third-party and supply chain vulnerabilities as their greatest resilience challenge. That’s up from 54% in 2025. Yet only 27% of organisations simulate cyber incidents or conduct recovery exercises with their ecosystem partners. Only 33% comprehensively map their supply chain to understand threat exposure.
For Indian IT services giants like Infosys, TCS, Wipro, HCL Tech, this should be a wake-up call. These companies sit at the nexus of global enterprise supply chains. A breach in their systems doesn’t just affect them. It ricochets through Fortune 500 clients across continents.
The report highlights something called “inheritance risk”. It’s the inability to assure the integrity of third-party software, hardware, and services. It ranked as the top supply chain concern across industries. In an age where Indian companies are embedding themselves deeper into global value chains, this risk travels both ways.
What Resilient Organizations Do Differently
The report isn’t all doom. It identifies clear patterns among organisations that rate themselves as highly resilient.
First, board engagement matters. Some 99% of highly resilient organisations report board involvement in cybersecurity. This is not done as a compliance checkbox, but as active oversight. In contrast, 13% of insufficiently resilient organisations report zero board engagement.
Second, they invest in ecosystem security. Highly resilient organisations are 44% more likely to simulate cyber incidents with partners, and 74% more likely to assess supplier security maturity.
Third, they govern AI proactively. Among highly resilient organisations, 71% conduct periodic security reviews of AI tools before deployment. Among insufficiently resilient ones, that number drops to 20%.
The differentiator isn’t budget. It’s mindset. Resilient organisations treat cybersecurity as a strategic function, not an IT cost centre. They recognise that in 2026, digital resilience is business resilience.
The Uncomfortable Truth
There’s a takeaway that Indian businesses and policymakers need to internalise. Cybersecurity is no longer about protecting data. It’s about protecting economic value, supply chains, critical infrastructure, and increasingly, national security.
The WEF report puts a number on it. The average significant cyberattack costs businesses approximately $250,000. The World Bank suggests reducing major cyber incidents could boost GDP per capita by 1.5% in developing economies.
India, that’s targeting a $5 trillion GDP and positioning itself as a global manufacturing alternative, the cyber question isn’t peripheral. It’s fundamental.
The organisations that thrive won’t be those that never get breached. They’ll be the ones that build the strongest capability to detect, respond, and recover. In cybersecurity, as in business, survival increasingly belongs to the resilient.
In other news, have you been checking out the crosswords below these articles? Try them out for yourselves, and see how quickly you can solve them!
Until next time, ReadOn!
ReadOn Insights Crossword 16-01-2026
Hints:
Across:
3: Head of the World Diamond Council, who stated that the lab-grown diamond bubble has burst.
6: The market effect in which lab-grown diamonds replace demand for natural diamonds in some global markets.
8: The natural diamond major whose CEO praised Titan’s no-exchange policy between lab-grown and natural diamonds.
9: The lab-grown diamond jewellery brand launched by Titan, with its first exclusive store.
10: The Indian city that houses thousands of lab-grown diamond manufacturing units.
Down:
1: A persistent global pricing trend where lab-grown diamond prices continue to fall over time.
2: The Indian jewellery major that launched its first lab-grown diamond brand in December 2025.
4: The global jewellery giant that shifted entirely to lab-grown diamonds in 2021.
5: The city where Titan opened its first exclusive lab-grown diamond jewellery store.
7: The strategy Titan is relying on to sell natural diamonds and lab-grown diamonds as separate categories, without overlap.
To solve this puzzle, click here!